What should a bank choose between HSM, MPC and TSS for digital asset custody?

We are sometimes asked about the merits of multi-party computation (MPC) methods in the context of transaction signature in custody solutions. Some would compare MPC to HSM-based solutions, as if the two approaches were mutually exclusive and if one of the two was inherently superior. We believe that this view is an oversimplification, as the MPC vs. HSM debate only concerns the transaction-signature layer, which is an important layer but just one among others described in section II. As we will discuss, HSM and MPC achieve different goals, serve different use cases, and may work together.
The role of an HSM
A hardware security module (HSM) is one approach to create a trusted execution environment (TEE) * , which in the context of a custody solution aims to:
● Securely store cryptographic values (such as blockchain account seeds, keys, but also other values such as authentication tokens, as well as certificates);
● Ensure that the logic executed in the HSM is done as prescribed, and that it does not reveal sensitive information (for example, when applying security controls such as those of the risk management layer, and when creating and signing transactions).
A state-of-the-art HSM notably relies on tamper detection systems in order to reset itself when a threat is detected, as well as code signing mechanisms to only run authorized code. More generally, the use of an HSM facilitates the risk analysis by providing a clearly identifiable trusted computing boundary (TCB), which has been certified to offer a certain level of security assurance. HSMs have been in production for decades for a reason and we believe are here to stay. For example, AWS and Google Cloud Platform provide “cloud HSM” services.
The role of MPC
MPC is a recent development in custody solutions and has a different purpose than HSMs: it is a class of cryptographic techniques that allows a set of participants to collectively issue a signature by running a protocol that does not expose the key. In particular, threshold signature schemes (TSS) allow t-of-n quorums. MPC therefore focuses on the signature part of the transaction layer. As of today, multiple TSS protocols exist, which differ in terms of adversarial model, security assurance, features (presigning, reshare, abort), protocol rounds (for setup, signing, and other stages). MPC is thus a tool of choice to mitigate the risk when only software components are used. For example, when a mobile phone application and a server application share control of a key. MPC can thus address selected use cases that purely HSM-based custody may not address, because dedicated hardware cannot be used.
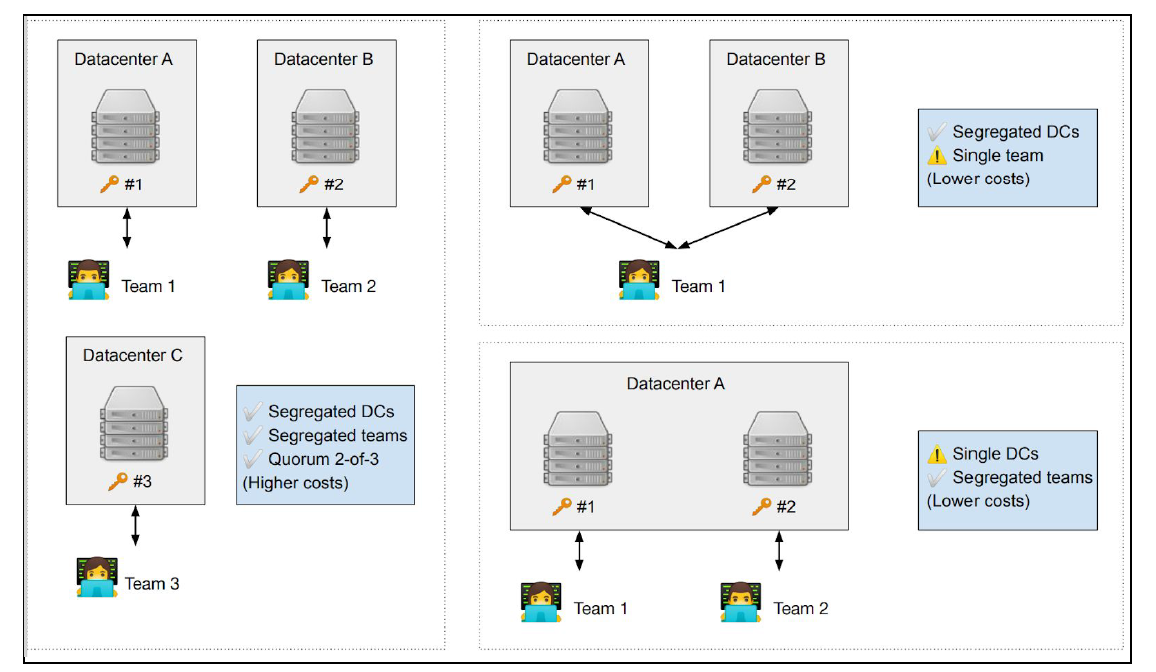
In principle, the shared control functionality that MPC offers can be achieved with a trusted execution environment, with the additional benefit that security controls can be enforced in a secure environment. Among current limitations of MPC-based technologies, note that most TSS protocols can only distribute the signing with a given key, as opposed to a full wallet using BIP32 derivation. Furthermore, back-ups as well as a key ceremony remain necessary. MPC and TSS can be nonetheless relevant tools that could even be combined with HSMs to achieve different types of deployment trade-offs. When assessing an MPC-based solution, one should evaluate whether it matches their scalability needs (2-party vs. multi-party), as well as the operational risk and cost of segregating the different nodes of the system. For example, different nodes, running on different data-centers, must be managed by different teams, such that no single administrator or access control solution can control multiple nodes at the same time (see Figure below). We recommend the 3-datacenter model (left-hand) as the most secure and reliable model.
Conclusion
At Taurus, we have implemented HSM-based solutions that we strengthened with our own firmware extension – now in production with the full spectrum of financial institutions** . They work and scale well. We have also closely followed the evolution of MPC and TSS assessing the maturity and relevance of known protocols and implementations. In this context,
- We have notably published some research, such as the article Attacking Threshold Wallet***
- We are using MPC technology for two use cases: (1) enable banking-grade full SaaS custody, (2) Augment HSM-based solutions. You will hear more about it soon as we recently joined the MPC alliance
That said, one of our conclusions is that a trusted execution environment (such as an HSM) is mandatory for high-assurance digital asset custody, with or without MPC.
*Note that the concepts of TEE and TCB were already rigorously defined in the 1985 “Orange Book”: https://csrc.nist.gov/csrc/media/publications/conference-paper/1998/10/08/proceedings-of-the-21st-nis sc-1998/documents/early-cs-papers/dod85.pdf.
**Systemic banks, investment banks, private banks, retail banks, crypto-banks and financial market infrastructure providers. Taurus SA, October 2020
*** Taurus SA - Technology paper October 2020